Network Penetration Testing
The systems, applications and network devices comprising your internal and external network infrastructures are continuously exposed to attacks from a growing number of skilled attackers. Identifying security weaknesses proactively is crucial to protect your systems, both your users and your own confidential information and ultimately your business.
Amplia Security can help you identify security vulnerabilities present in your internal and external networks infrastructure, we will provide advice on how to remediate issues found, determine the current security stance of the networks analyzed and give you overall recommendations.
Testing the security of your network infrastructure will allow you to:
About Our Methodology
Penetration Testing is the most efficient way to accurately identify security vulnerabilities. It is a method used to evaluate the security of a network, web application, web service, and any other software system or device by using the techniques a hacker would use in a safe and controlled manner.
Amplia Security Penetration Testing Methodology is the result of over 20 years of experience. We focus on manual testing of the systems which allows for the detection of logic flaws and complex vulnerabilities with the help of automated tools to obtain the best results in a time efficient manner.
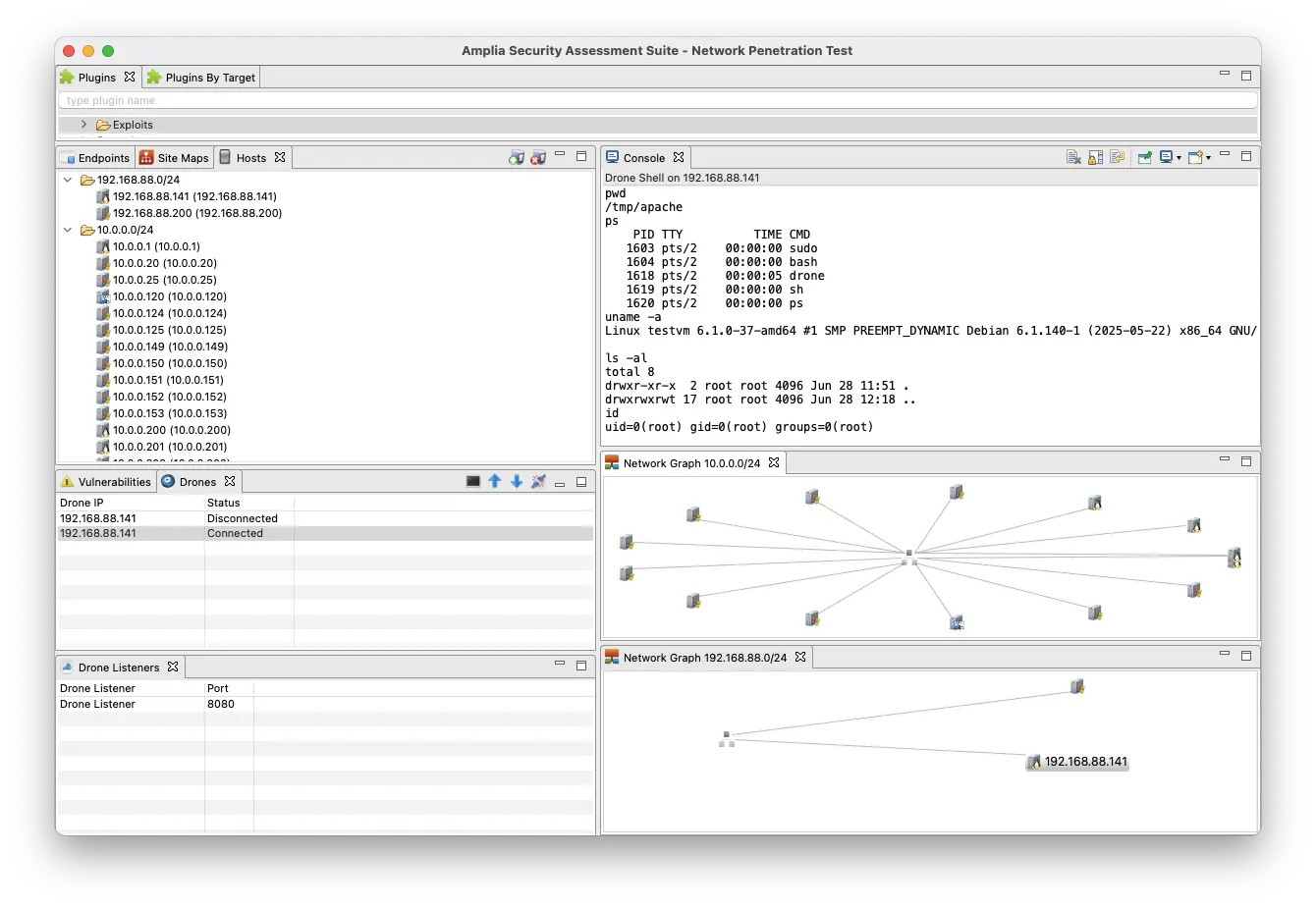
Tasks performed during a Penetrarion Test include:
Checks performed include and go beyond the following:
Our methodology is aimed at finding known and also previously unknown vulnerabilities using different techniques including reverse engineering, instrumentation, manual fault injection, automated fuzzing, creation of custom tools and proof-of-concept code.
if you want more information about our services, need a quotation, or have any other question, please email us at info@ampliasecurity.com.
